Over 40% of all websites worldwide use WordPress. This Content Management Systems owes its popularity to the open-source codebase and the possibility to extend the core functionality of the website via third party plugins – there are more than 59 thousand official plugins currently available.
Plugins are in most cases developed by independent software companies and professionals with different levels of expertise and security awareness. Before being added to the official WordPress library, plugins are audited to ensure they work as they are intended to, but also that they follow WordPress’s security guidelines. However, not even the most efficient review team can test WordPress plugins under the lens of cyber security and grant they are 100% cyber secure. Also, consider plugins are checked only when first added to the WordPress repository.
Lots of other plugins are available outside the official library. In most cases, they are cracked or alternative versions of fee-based plugins, which can be downloaded from free but may embed backdoors. For these reasons, you may not be surprised to read that in 2021 about 98% of vulnerabilities concerning WordPress websites were related to plugins.
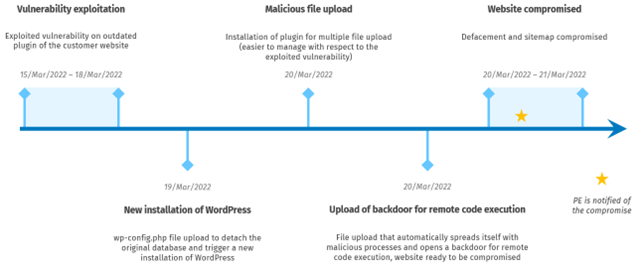
An outdated plugin ignited the compromise of the website of one of our customers. During routine content update, its digital marketing team was unable to access the administration panel: the anomaly was suspicious enough to promptly call for an investigation about this issue. Paradox Engineering’s cyber security team analyzed the case, pointed out a cyber security incident and detected two attack vectors with different goals.
The first attack aimed at manipulating the home page of the website (so called ‘website defacement’), the second was likely to host a hidden ecommerce website to sell illegal goods. The attackers exploited an outdated and vulnerable plugin to upload a modified configuration file, which triggered a new WordPress installation on the host machine. The new installation process allowed attackers to upload other malicious files to gain full control of the website.
In less than a week, the site would have become a valuable resource in the hands of cyber criminals. Fortunately, the request for investigation came to PE a few hours after the malicious files were uploaded, so it was possible to impede the website defacement. The early intervention reduced the time of compromise, leading to the clean-up of the website within a few hours.
Paradox Engineering’s incident management process is based on NIST best practices to mitigate the impact of the attack and speed up recovery. The first step is to collect as many data as possible regarding the events that occurred in the attacked system and extract relevant information about the attack vectors. After the assessment, it is important to quickly implement all necessary containment actions to block other possible attack movements. Finally, after the containment, a deep investigation to find the root cause is useful to define the best resolution and mitigations actions to prevent similar attacks in the future.
7 tips to protect your website:
- implement advanced authorization and authentication website backup policies – store the backup in a safe place (not accessible from the web instance) and always use backup solutions that are not provided by CMS plugins
- prefer policies that follow the main principles of “need to know” and “least privilege”
- install only strictly necessary plugins and regularly delete the ones you don’t use
- keep the CMS and plugin updated. It’s recommended to set automatic updates for security patches and manually apply major releases
- have a staging environment to test any update
- collect log events for the cybersecurity team to detect anomalies
- implement a change detection mechanism (e.g., through hashes) to notify the cybersecurity team in case of suspicious website access or modification